Link to disk image.
Link to memory image.
Hashes.
Password for disk image.
Here's my write-up for Ali Hadi's "Web Server Case". This is a simple case but enjoyable because you can correlate disk artifacts and memory to build the picture of attacker activity. I'll write this up as I go so that anyone could follow along (note: this is more of a walkthrough than a report).
Ali provided 7 main questions to guide analysis:
- What type of attacks have been performed on the box?
- How many users has the attacker(s) added to the box, and how were they added?
- What leftovers (files, tools, info, etc) did the attacker(s) leave behind? (assume our team arrived in time and the attacker(s) couldn’t clean and cover their tracks)
- What software has been installed on the box, and were they installed by the attacker(s) or not?
- Using memory forensics, can you identify the type of shellcode used?
- What is the timeline analysis for all events that happened on the box?
- What is your hypothesis for the case, and what is your approach in solving it?
Gather System Information:
My first step was to get some contextual information on the system. I mounted the image using FTK imager (make sure to always mount as "Filesystem / Read-only" to ensure your tools work as intended) and extracted the desired registry hives (system, software, sam, ntuser.dat, usrclass.dat).
I used Eric Z's Registry Explorer and Harlan C's RegRipper to get two different views of the System and Software hives. I often use both of these tools to verify against each other. I also prefer Explorer for less structured analysis, and RegRipper for getting all the common answers I need on every case (Reg Explorer does this too with Bookmarks, but I like some of the auto-conversions in RegRipper and it's just a tool I'm comfortable with honestly).
Computer Name: WIN-L0ZZQ76PMUF
Time Zone: PDT (ActiveTimeBias is -7UTC)
Since this is a pretty obvious practice scenario created for a college course, the instructor gives us easily spotted pivot points. The "Account Created" times for the "user1" and "hacker" accounts are the first critical items we can add to our timeline and pivot from.
Get Organized:
It always pays dividends when I take a few minutes to group my analytic questions to answer, write down what artifacts I expect to need to answer each question, and also write down any unknowns that I don't currently have a plan for but need to be answered.
In this case we don't have much context other than: This is a web server. It has been hacked via a web service. The attacker has added some accounts. Other than these clues we have to figure it out ourselves, which puts extra emphasis on vetting out legitimate vs attacker activity.
- What types of attacks have been performed on the box? Expected to use web server logs, file system timeline, memory analysis (especially if web logs lack parameters which we can potentially fill in with memory).
- How many users did the attacker add? (hypothesis == 2 based upon SAM) and how were they added? To figure out how they were added we'll need to find the actual commands run, this might be in the web logs depending on the vulnerability exploited or in memory.
- What leftovers (files, tools, info, etc) did the attacker(s) leave behind? This sounds like a filesystem timeline ($MFT, $LogFile, $UsnJrnl:$J) task if I've ever heard one.
- Via Disk: right in the root of the drive you see a XAMPP folder suggesting the Windows LAMP stack is installed.
- Via Memory:
Netscan shows httpd.exe (Apache) is running and listening on 80/443.
PS C:\Users\aswood\Desktop\tools\Forensics\Memory Forensics\volatility_2.6_win64_standalone> .\volatility_2.6_win64_standalone.exe -f C:\Users\aswood\Desk
top\Cases\Challenge1_WebServerCase\memdump\memdump.mem --profile=Win2008SP2x86 netscan
Pslist (or psscan/psxview) shows that Mysqld.exe, httpd.exe, and xampp-control.exe are running.
PS C:\Users\aswood\Desktop\tools\Forensics\Memory Forensics\volatility_2.6_win64_standalone> .\volatility_2.6_win64_standalone.exe -f C:\Users\aswood\Desk
top\Cases\Challenge1_WebServerCase\memdump\memdump.mem --profile=Win2008SP2x86 pslist
XAMPP is a prepackaged LAMP stack which has packages for Windows, Linux and OSX. It's really focused on ease of use and setup, which often leads to default and insecure configurations being used in production. We still have the image mounted as E:\ drive so viewing the logs is as simple as accessing "E:\[root]\xampp\apache\logs".
As with any Apache install, the access.log is the key artifact that will show us what requests were made to the server. In this case it's really simple to start finding answers to our questions using the time period of the account creation (Sept 2 2015 ~0900 UTC) and the account names (hacker, user1) as a pivot point.
A simple search through the access.log for the minute of the account creation has interesting results:
We see a series of POST's to "/dvwa/vulnerabilities/exec" with a 200 response. DVWA is "Damn Vulnerable Web App" a common teaching tool for basic web application pen-testing (fun if you've never worked through it, highly recommended as well as most things on VulnHub). Here's what the "vulnerabilities/exec/" page looks like in DVWA:
Essentially it's an insecure web front-end for the ping command. The page doesn't perform any input validation, allowing anyone to end the ping command and run another command. Example: "192.168.0.1; rm -rf /" ("ouch" says linux server running apache2 as root!)
Creating Filesystem Timeline:
There are many tools that can create a functional filesystem timeline. Here are some options:
- Absolute Fastest/Laziest MFT based: FTK Imager can create a "Directory Listing" which contains MAC times (right click in evidence tree, select "Export Directory Listing".
- Sleuthkit FLS & Mactime can be used to create a filesystem timeline in NTFS.
- Log2timeline/Plaso can be used to create a filesystem timeline.
- A simple MFT parsing tool like RedWolf MFT_Parser or AnalyzeMFT.py
I opted for something a little overkill and cool by using David Cowen's Triforce (ANJP 3.11.07 free edition) tool. It doesn't hurt that Zelda just came out. This tool accepts not just the $MFT but also the $J and $LogFile, putting pretty much all the filesystem metadata available on disk in your hands to interpret. Parse these files using ANJP, connect to the database, and finally export any filtered views you need to review to text or XLSX.
What are the first two "Deleted" records reported from the USN Journal? How about two artifacts of php shells dropped via SQL injection? #mastersword
Creating Volatility Compatible Memory Strings file:
You can simple run strings against a memory dump and use command line tools to find items of interest. This is the oldest form of memory forensics and is still very useful. Volatility takes that technique to another level by telling you what processes space the string appears in! This can actually be done in (at least) two different ways. One simple way I've used many times is with the Volatility "yarascan" module. By using the --yara-rules "mystring" you can search for one string (or a YARA rule full of strings with the --yara-file switch) and find what process it resides within.
To do this at scale - you can use the Volatility strings module which requires an input file of the strings preceded with their decimal offset within the memory dump. Strings.exe from Sysinternals can produce this output with a command similar to the below:
After this is created you can run this output file through Volatility with the "strings" module to produce another file with the process mapping for every string! This is a technique I don't generally use, so I was excited to put it to work after reading about it in the crucial tome "Art of Memory Forensics" (highly recommended if you don't own it - enjoy it over the course of several months IMO :-) ).
Attack: Command Injection
This leads us to the first attack against this box - command injection. Looking at our access.log for the POST's to "dvwa/vulnerabilities/exec/" shows that we do not have the parameters supplied to the web server. As far as I know - there isn't an on-disk artifact in this case which shows the commands run to create the accounts so we need to pivot to memory.
Using Volatility (I'm using 2.6 standalone Windows version from here) the first commands that come to mind are "consoles" and "cmdscan". Essentially consoles is the newer plugin and will show us both the command and result.
PS C:\Users\aswood\Desktop\tools\Forensics\Memory Forensics\volatility_2.6_win64_standalone> .\volatility_2.6_win64_standalone.exe -f C:\Users\aswood\Desk
top\Cases\Challenge1_WebServerCase\memdump\memdump.mem --profile=Win2008SP2x86 consoles
The "consoles" module shows us the commands run to create the "user1" account, add it to the "Remote Desktop Users" local group, and enable RDP in the Windows firewall. Note that at this time we don't have confirmation that the "user1" account was added via the DVWA command execution vulnerability, it's simply a hypothesis.
Well that's great - but what about the "hacker" account? It's not in the consoles display like the creation of "user1". We know the command execution vulnerability is being served up by the HTTPD.exe process, so lets dump the memory space from that process (or processes) and string search them.
To do this I used the "memdump" module in Volatility as below to dump the process space of the two httpd.exe processes to my Artifacts directory.
After you've dumped the process space, you can simply string search the files. I created text files of all strings with the Sysinternals strings program. After you've created your lists of strings you can simply search them using Select-String or Grep.
Alright! At the bottom we see the "net user hacker hacker /add" and "net localgroup "Remote Desktop Users" hacker /add" commands. Take note of the %26%26 before the commands - this shows that the attacker was submitting a ping request through the DVWA web app for 192.168.56.102 (his own IP) then typing && (%26%26 in URI encoding) to break out of the ping command and run additional commands. Interestingly we do not have the same results for the "user1" account which was added just 19 seconds before the "hacker" account. This leads me to hypothesize that these two accounts were added in different ways.
That last discovery gives us another pivot (queue Zelda sound)! "%26%26 (&&) can serve as a relatively unique pattern representing commands run via the DVWA command injection vulnerability.
Using this pivot we do see some additional recon activity (directory listings of the "Windows" and "Users\Administrator" directories) but not much else. It definitely appears this exploitation was primarily used as an example and to create the "hacker" account.
Attack: SQL Injection
Using the access.log we can observe the SQLmap SQL injection ("SQLi") tool default user agent string and fairly obvious SQLi behavior starting at 11:15:40. Because these attacks were run against the "/dvwa/vulnerabilities/sqli page it did not take long for the SQLi attack to gain a shell.
SQLmap writing a simple shell to disk:
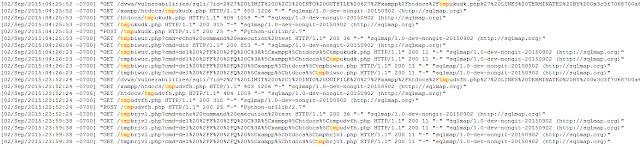
At 11:25:53 two files are dropped on the box "tmpbiwuc.php" and "tmpukudk.php". Within the same second we see a GET request for "tmpbiwuc.php" intended to run the command "echo command execution test". At 11:26:23 the "tmpukudk.php" file was deleted by a command issued by through the SQLmap created shell.
On 9/3/15 @ 6:52:24 another SQLi attack succeeds and new PHP shells are dropped "tmpudvfh.php" and "tmpbrjvl.php". Once again the initial file "tmpudvfh.php" is deleted via a subsequent command. I have been on the serving end of SQLmap many times in the past, but relatively few times on the receiving end of an attacker getting a command shell directly through SQLmap. I hypothesize this is normal behavior for SQLmap to create an initial dropper, create a more full featured shell, then delete the dropper, but I haven't verified this.
Attack: Local File Inclusion
There are obvious indicators of local file inclusion in the access.log. The attacker appears to utilize a LFI vulnerability in "/dvwa/vulnerabilities/fi/" to read multiple sensitive files on disk and to read files which the attacker themselves wrote to disk via other methods. Reading an attacker written local file is the bridge between a RFI ("Remote File Inclusion") and LFI, and usually allows command execution.
1. Attacker uses LFI to read the Windows hosts file.
2. Attacker uses LFI to read "data.txt" which contains "Hello". Appears to be a test file.
3. Attacker uses LFI to read PHPmyadmin configuration.
4. Attacker uses LFI to read abc.txt an attacker created file with potential code execution.
Attacker Tools: Webshells
On 9/3/2015 at 7:14:48 a file "webshells.zip" is created in the "DVWA" folder. This archive contains the infamous C99 webshell, as well as a very basic PHP shell that simply accepts a shell command as a parameter.
The basic "phpshell.php" (and "phpshell2.php" duplicate) were used several times notably to create the "abc" folder:
Times that commands were submitted via the C99 shell (found using access.log):
Timeline:
| Time (UTC) | Event | Source | Notes |
| 9/2/2015 7:10:41 | First web requests from 192.168.56.102 with useragent suggesting potential Kali Linux / IceWeasel browser | access.log | Fast requests - potential spidering or directory brute force (dirb?) "Mozilla/5.0 (X11; Linux x86_64; rv:38.0) Gecko/20100101 Firefox/38.0 Iceweasel/38.2.0" (I don't think many people install Iceweasel, it's installed in Kali so that's probably what was used.) |
| 9/2/2015 8:34:27 | 192.168.56.102 switches to UA "Mozilla/4.0 (compatible; MSIE 6.0;)" suggesting potential change in tool used | access.log | |
| 9/2/2015 8:35:47 | 192.168.56.102 switches to UA ""Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)"" suggesting potential change in tool used | access.log | |
| 9/2/2015 9:04:35 | HTTP POSTS to /dvwa/vulnerabilities/exec | access.log | Time correlation to creation of user1 && hacker accounts. Hypothesis - attacker used command injection vulnerability to create these accounts |
| (assumed proximity BEFORE account creation) | net user user1 Root@psut /add | Memory strings | Run via apparent command injection vuln |
| (assumed proximity BEFORE account creation) | net localgroup "Remote Desktop Users" user1 /add | Memory (found with Vol "consoles" plugin) | Run via apparent command injection vuln |
| 9/2/2015 9:05:06 | user1 account created | SAM hive | Initial pivot |
| (assumed proximity BEFORE account creation) | net user hacker hacker /add | Memory strings | Run via apparent command injection vuln |
| (assumed proximity BEFORE account creation) | net localgroup "Remote Desktop Users" hacker /add | Memory strings | Run via apparent command injection vuln |
| 9/2/2015 9:05:25 | hacker account created | SAM hive | Initial pivot |
| 9/2/2015 9:31:16 | First LFI activity observed - accessing hosts file | access.log | Hypothesis - attacker accessed hosts file to confirm they have LFI access |
| 9/2/2015 9:33:23 | "GET /dvwa/vulnerabilities/fi/?page=../../../../../../users/administrator/data.txt HTTP/1.1" 200 | access.log | Attacker accesses data.txt which simply says "hello" inside. Hypothesis - attacker created this file with command injection vuln, and accessed it via LFI to verify file write capability and access via LFI. |
| 9/2/2015 9:34:52 | LFI activity observed accessing phpmyadmin configuration. | php_error_log && access.log | PHP Warning: include(../../../../../../xampp/phpmyadmin/config.inc): failed to open stream: No such file or directory in C:\xampp\htdocs\DVWA\vulnerabilities\fi\index.php on line 35 |
| 9/2/2015 9:42:11 | "POST /dvwa/vulnerabilities/exec/ HTTP/1.1" 200 4951 "http://192.168.56.101/dvwa/vulnerabilities/exec/" | access.log | Hypothesis - attacker wrote abc.txt using command injection vuln. |
| 9/2/2015 9:42:21 | "GET /dvwa/vulnerabilities/fi/?page=../../../../../../../../abc.txt HTTP/1.1" 200 | access.log | Hypothesis - attacker used abc.txt |
| 9/2/2015 10:49:53 | "GET /dvwa/vulnerabilities/sqli/?id=a%27+or+1%3D1&Submit=Submit HTTP/1.1" 200 159 "http://192.168.56.101/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit" | access.log | SQLi activitry |
| 9/2/2015 11:15:40 | "GET /dvwa/vulnerabilities/sqli/?id=2&Submit=Submit HTTP/1.1" 302 1 "-" "sqlmap/1.0-dev-nongit-20150902 (http://sqlmap.org)" | access.log | SQLmap attack tool run by attacker, evidenced by UA string and accompanying SQLi attempts. |
| 9/2/2015 11:25:53 | tmpbiwuc.php created time | MFT | Potential malicious PHP webshell |
| 9/2/2015 11:25:52 | tmpukudk.php created time | MFT | Potential malicious PHP webshell |
| 9/2/2015 11:25:53 | "GET /tmpbiwuc.php?cmd=echo%20command%20execution%20test HTTP/1.1" | access.log | Command execution test of droppecd tmpbiwuc.php file which was dropped by SQLmap. |
| 9/3/2015 7:14:48 | \xampp\htdocs\DVWA\webshells.zip created | MFT | PHP webshells - C99 and a simple 1 liner PHP command shell |
| 9/3/2015 7:16:03 | phpshell.php accessed | php_error_log | |
| 9/3/2015 7:19:32 | c99.php accessed | php_error_log | |
| 9/3/2015 7:21:28 | c99 shell used to execute 4 commands | access.log | Shows attacker persistence using Webshell. |

















No comments:
Post a Comment